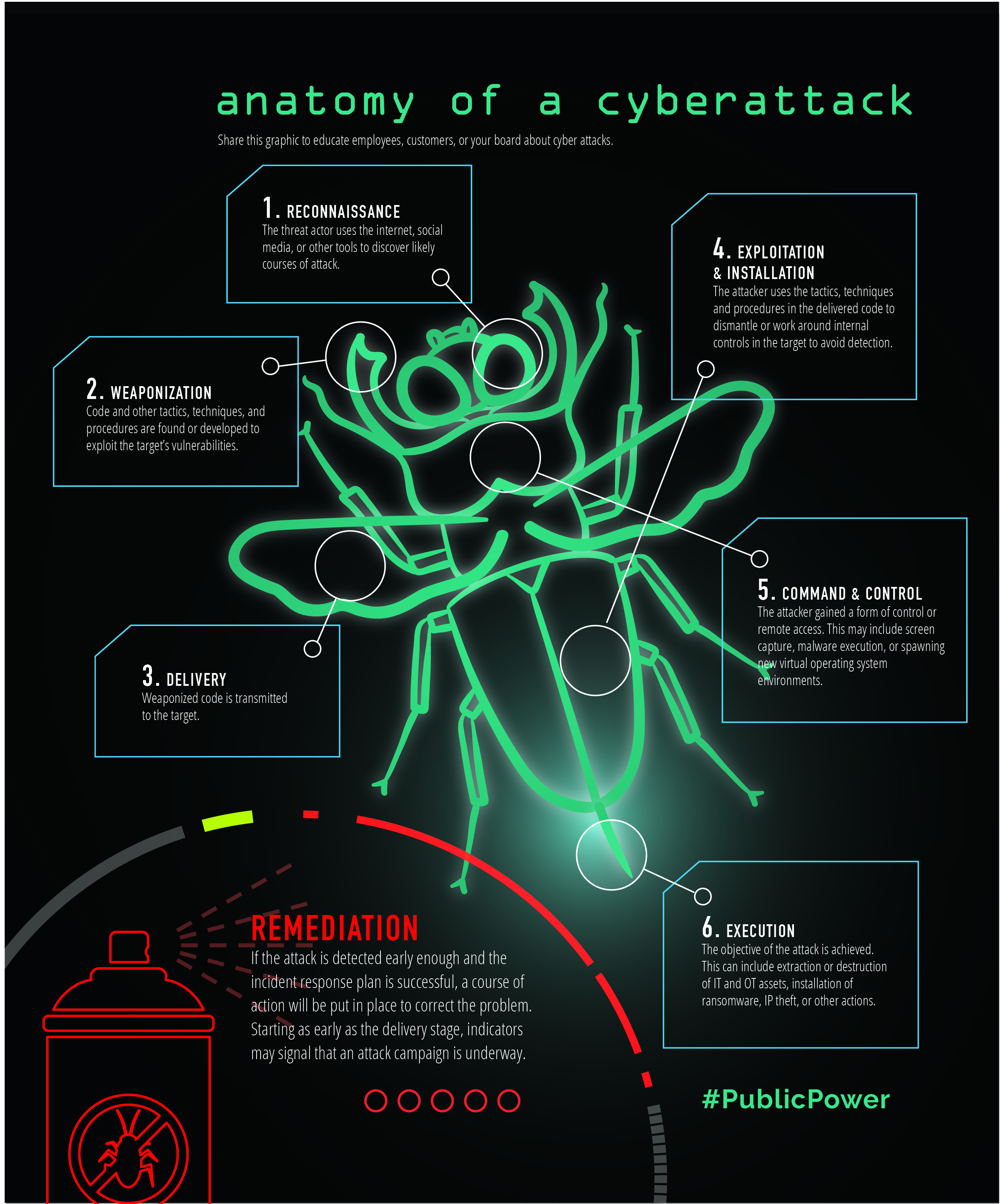
Anatomy of a cyber attack
- Reconnaissance – The threat actor uses the internet, social media, or other tools to discover likely courses of attack.
- Weaponization – Code and other tactics, techniques, and procedures are found or developed to exploit the target’s vulnerabilities.
- Delivery – Weaponized code is transmitted to the target.
- Exploitation and Installation – The attacker uses the tactics, techniques and procedures in the delivered code to dismantle or work around internal controls in the target to avoid detection.
- Command and Control – The attacker gained a form of control or remote access. This may include screen capture, malware execution, or spawning new virtual operating system environments.
- Execution – The objective of the attack is achieved. This can include extraction or destruction of IT and OT assets, installation of ransomware, IP theft, or other actions.
Remediation – If the attack is detected early enough and the incident response plan is successful, a course of action will be put in place to correct the problem. Starting as early as the delivery stage, indicators may signal that an attack campaign is underway.